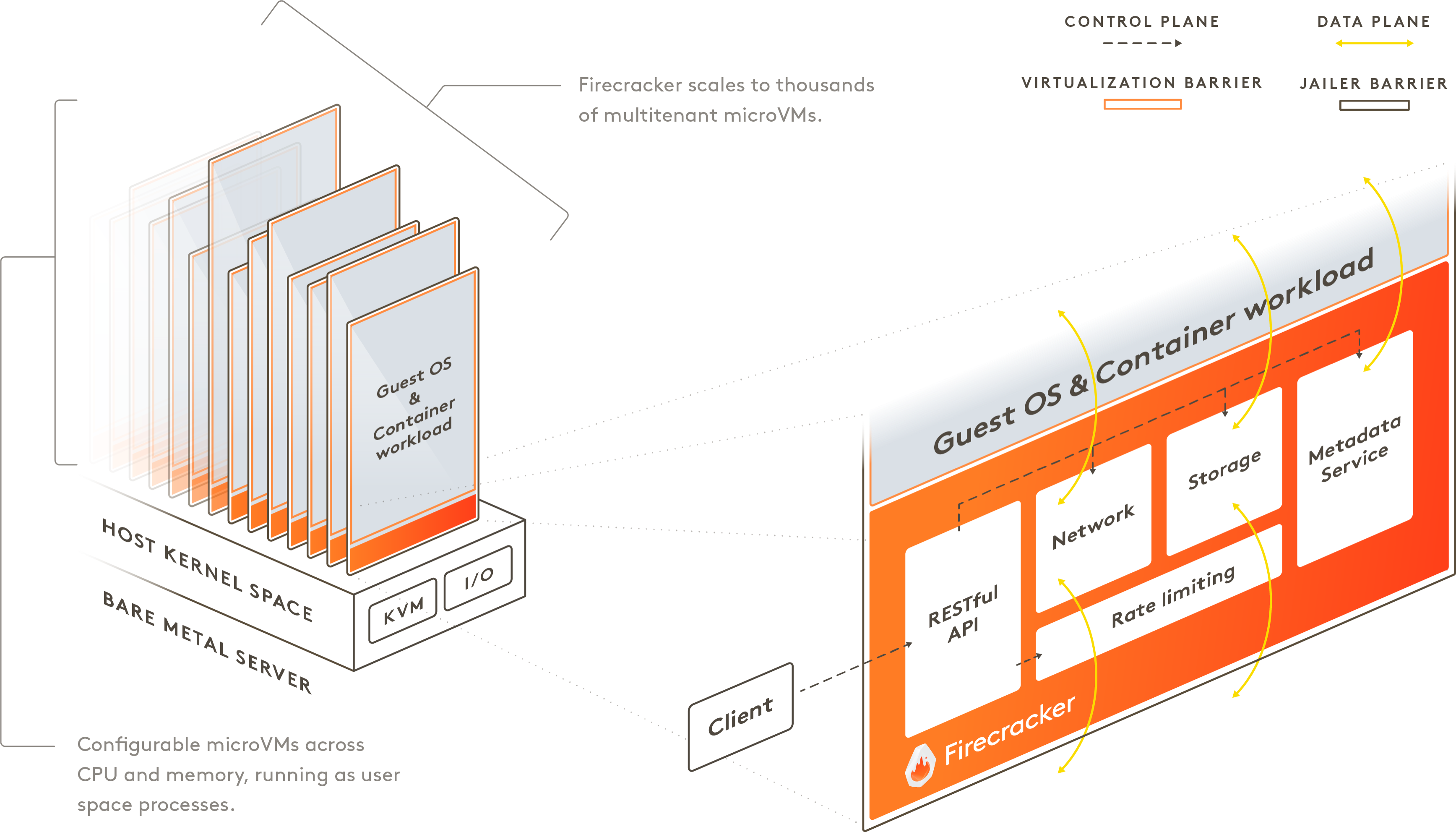
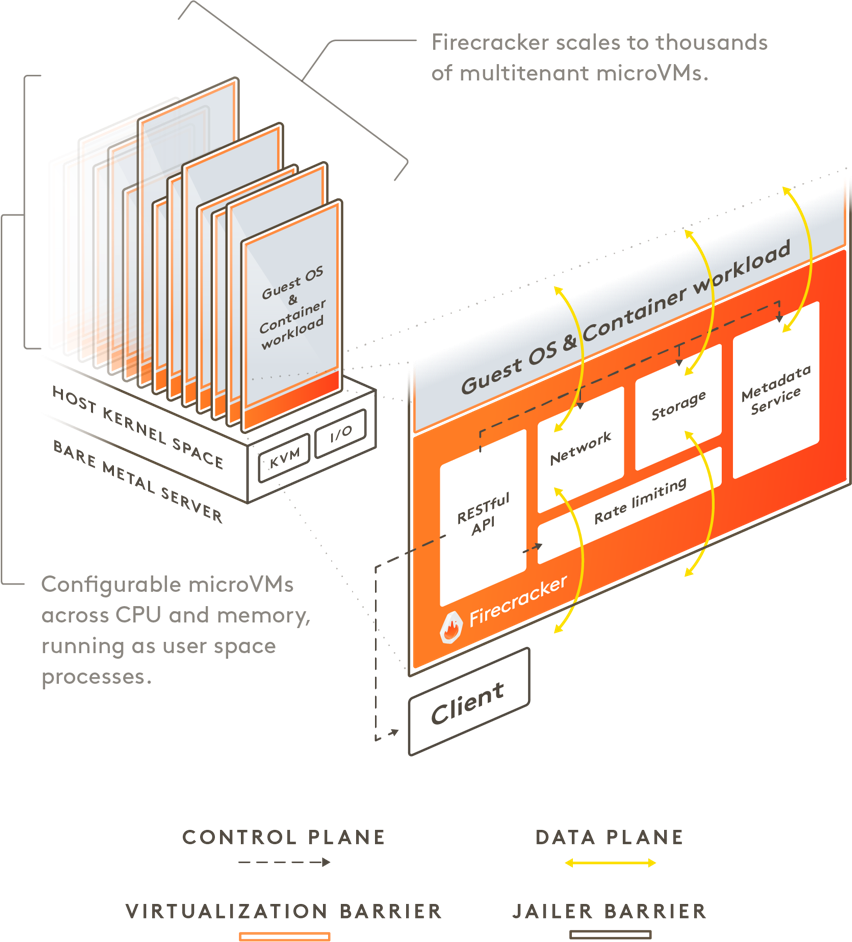
Firecracker enables you to deploy workloads in lightweight virtual machines, called microVMs, which provide enhanced security and workload isolation over traditional VMs, while enabling the speed and resource efficiency of containers. Firecracker was developed at Amazon Web Services to improve the customer experience of services like AWS Lambda and AWS Fargate .
Firecracker is a virtual machine monitor (VMM) that uses the Linux Kernel-based Virtual Machine (KVM) to create and manage microVMs. Firecracker has a minimalist design. It excludes unnecessary devices and guest functionality to reduce the memory footprint and attack surface area of each microVM. This improves security, decreases the startup time, and increases hardware utilization. Firecracker is generally available on 64-bit Intel, AMD and Arm CPUs with support for hardware virtualization.
Firecracker is used by/integrated with (in alphabetical order): appfleet, containerd via firecracker-containerd, Fly.io, Kata Containers, Koyeb, Northflank, OpenNebula, Qovery, UniK, webapp.io, and microvm.nix. Firecracker can run Linux and OSv guests. Our latest roadmap can be found here.